By Raphael Kapsamer – Partner Development Manager, Tributech
Log data plays a critical role in security operations by providing insights into system events and network activity. It serves as a valuable resource for identifying security threats, monitoring system performance, and detecting anomalies. This makes log data a popular target for different cyber-attacks. Cybercriminals or malicious insiders can modify log data, concealing their activities and making it difficult for security teams to identify and respond to security incidents. This article covers the importance of log data, the techniques attackers use to tamper with it, gives examples of cyber-attacks where log data has been tampered with, and explains best practices for protecting log data integrity.
WHAT IS LOG DATA AND HOW IS IT USED BY SECOPS TEAMS?
Log data is a record of events and activities generated by devices, applications, and systems. This data can include network traffic, system logs, user activity, and other information that provides a detailed picture of system operations. SecOps teams rely on log data to identify security threats, investigate incidents, and monitor system performance. By analysing log data, security analysts can identify patterns and anomalies that may indicate malicious activity or system errors. Log data is also used for compliance and auditing purposes to ensure that systems are operating in accordance with industry standards and regulatory requirements.
HOW LOG DATA CAN GET TAMPERED WITH
Attackers can use various techniques to tamper with log data, including log injection, log deletion, and log alteration.
Log Injection: Log injection involves injecting false or malicious log entries into log files. Attackers use this technique to obfuscate their activities, misdirect investigators, or create false narratives. Here are some key aspects of log injection:
- Techniques: Attackers can inject logs by exploiting vulnerabilities in the logging infrastructure, abusing log input fields or APIs, or directly modifying log files to add new entries. This can include injecting SQL statements, command injections, or modifying log message formats.
- Impact: Log injection can lead to false alarms, divert attention from actual security incidents, or manipulate the results of security monitoring and analysis. It can hinder accurate threat detection and response by flooding the logs with irrelevant or misleading information.
- Point of attack: Log injection can occur at different stages in the data pipeline. It can happen at the source system before logs are transmitted, during transit if logs are intercepted and modified, or at the central log storage where all logs are processed and stored.
Log Deletion: Log deletion refers to the act of removing or erasing log entries from log files, which can be done to conceal malicious activities or hide evidence of unauthorized access. Attackers may target log files to hinder incident investigations, cover their tracks, or avoid detection. Here are some key aspects of log deletion:
- Techniques: Attackers can delete logs through various means, such as exploiting vulnerabilities in log management software, manipulating file permissions to gain unauthorized access and delete entries, or directly modifying log files using administrative privileges.
- Impact: Log deletion can hinder forensic investigations, making it challenging to reconstruct the sequence of events during an incident. It can also impede auditing and compliance efforts, as vital information may be missing.
- Point of attack: Log deletion can occur at multiple points in the data pipeline. It can happen directly at the source system where logs are generated, during transit if logs are intercepted, or at the central log storage where all logs are stored.
Log Alteration: Log alteration involves modifying existing log entries to manipulate or misrepresent the information contained within them. Attackers may alter log entries to change the narrative, conceal their activities, or create false records. Here are some important aspects of log alteration:
- Techniques: Attackers can alter log entries by modifying timestamps, changing the content of log messages, manipulating metadata, or falsifying log events. This can be achieved through direct access to log files, exploiting vulnerabilities in logging software, or leveraging privileged access.
- Impact: Log alteration can distort the accuracy and reliability of log data, making it difficult to rely on for incident response, forensic analysis, or compliance audits. It can lead to misinterpretation of events and compromise the integrity of investigative processes.
- Point of attack: Log alteration can occur at various points of the data pipeline. It can happen at the source system before log data is transmitted, during transit if logs are intercepted and modified, or at the central log storage where all logs are stored and processed.
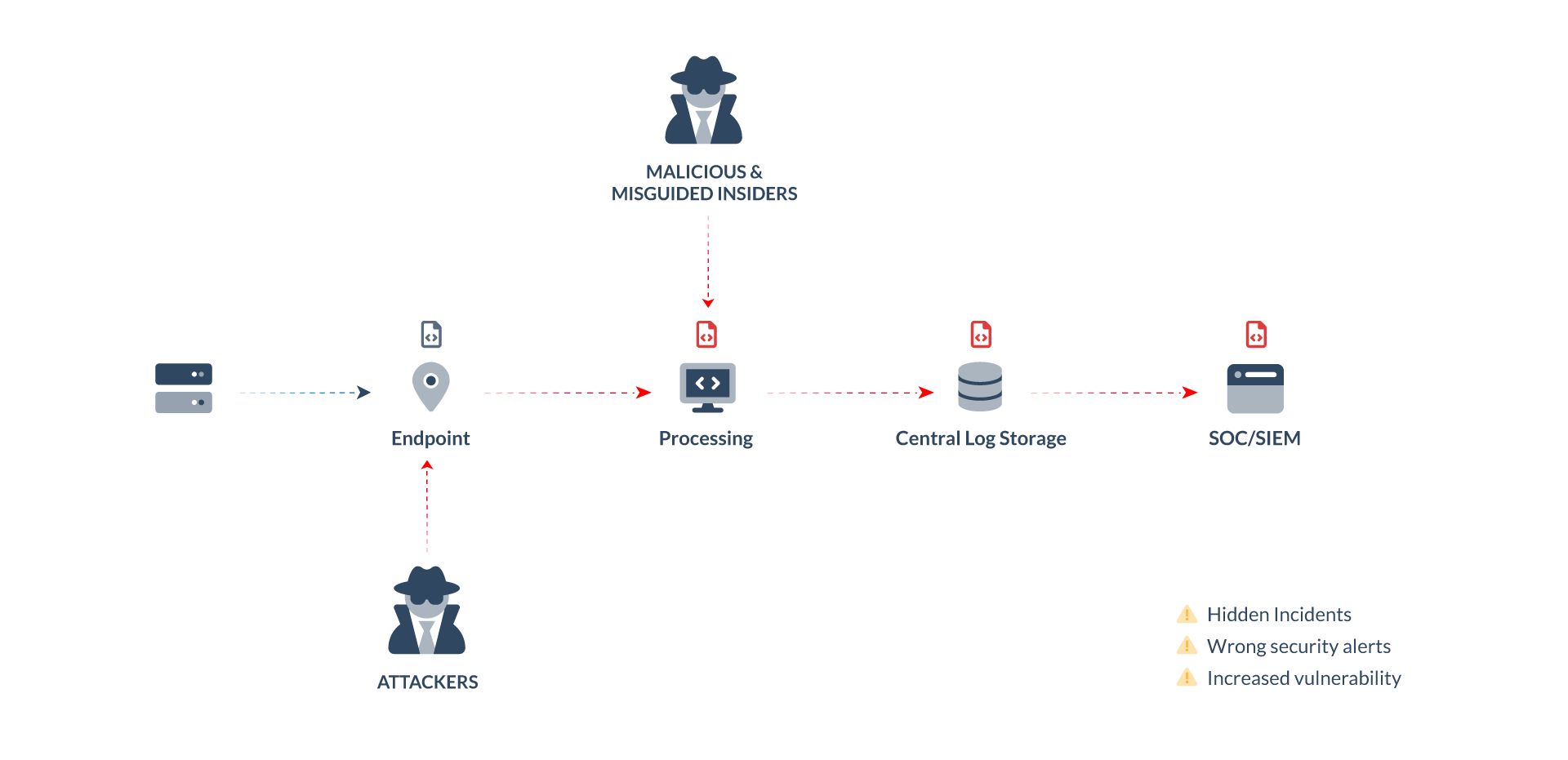
It can be observed that over the entire data pipeline, from the source until the SOC/SIEM, log data is under attack. Cyber criminals or malicious insiders can inject, alter, or delete logs in order to hide certain events. Understanding these techniques and their potential impact is crucial for organizations to implement robust security measures to prevent log tampering, ensure data integrity, and maintain reliable log records for effective incident response, forensic analysis, and compliance.
REAL-LIFE INCIDENTS OF LOG DATA TAMPERING
In recent years some of the most severe cyber-attacks had one attack pattern in common: Attackers tampered with log data to confuse SecOps teams, evade detection and cover their tracks. It can be observed that log data tampering has played an essential role in ransomware attacks, data breaches and supply chain attacks. Such as seen in the following incidents, which demonstrate the importance of ensuring the integrity of log data to detect and respond to cyber-attacks effectively:
Colonial Pipeline Ransomware Attack: In May 2021, Colonial Pipeline, a major fuel pipeline operator in the US, was hit by a ransomware attack that disrupted the company’s operations and caused widespread fuel shortages. As part of the attack, the attackers tampered with the company’s syslog data to cover their tracks and evade detection.
SITA Data Breach: In March 2021, it was reported that the airline IT services provider SITA had suffered a data breach that affected multiple airlines. According to reports, the attackers modified log files to hide the exfiltration of data and also deleted some logs entirely to further cover their tracks.
SolarWinds Supply Chain Attack: In December 2020, it was discovered that a sophisticated cyber-attack had been launched against SolarWinds, a company that provides network management software to numerous government agencies and Fortune 500 companies. As part of the attack, the attackers tampered with SolarWinds’ syslog data to evade detection and cover their tracks.
BEST PRACTICES TO PROTECT AGAINST LOG DATA TAMPERING
To protect against log data tampering, organisations can implement various best practices, such as:
- Implement data integrity controls: Implement data integrity controls such as checksums, digital signatures, and encryption to ensure that log data is not tampered with in transit or storage.
- Secure logging infrastructure: Ensure that the logging infrastructure is secure by following best practices for network segmentation, access controls, and monitoring.
- Monitor logs for anomalies: Regularly monitor log data for anomalies and irregularities that may indicate log tampering.
- Implement access controls: Implement access controls to restrict access to log data and ensure that only authorized personnel can modify or delete log files.
- Regularly backup log data: Regularly backup log data to protect against data loss due to tampering, hardware failure, or other incidents. This will ensure that the organisation can quickly recover from any incidents of log data tampering.
By implementing these measures, organisations can reduce the risk of log data tampering and ensure that their SecOps teams have access to accurate and reliable data to make informed decisions.
LIMITATIONS OF EXISTING DATA INTEGRITY CONTROLS
The two most common techniques to control log data integrity are hashing and signing and both have its limitations:
- Hashing: Hashing involves generating a unique hash value for log data and comparing it with the stored hash to detect tampering. However, hashing alone does not prevent tampering or deletion of logs, as an attacker can modify the hash or delete the logs without detection. Hashing also lacks non-repudiation, making it difficult to prove the integrity of logs to a third party.
- Signing: Signing, on the other hand, adds an extra layer of security by using digital signatures. Log entries are signed with a private key, and the corresponding public key is used for verification. This ensures that only the holder of the private key can sign the logs, providing some level of integrity and non-repudiation. However, signing does not prevent deletion or modification of logs, as an attacker can delete signed chunks or create fake logs with valid signatures.
Furthermore, the point when log data is hashed and/or signed is utterly important. If these techniques are implemented when logs arrive at the central log storage organisations have no visibility if log files have been tampered with before. In this scenario, the tampering would be undetected and tampered logs will be believed to be trustworthy even though they are not.
To effectively protect log data integrity it is necessary to implement those techniques directly at the point where log data is created.
HOW TRIBUTECH CAN HELP SECURE LOG DATA INTEGRITY
Tributech enables organisations to effectively implement the most crucial best practice by securing data integrity and authenticity end-to-end. Think about it the other way: When monitoring for anomalies, how accurate can that be when using tampered log data? What’s the point of backing up log data when data integrity is compromised?
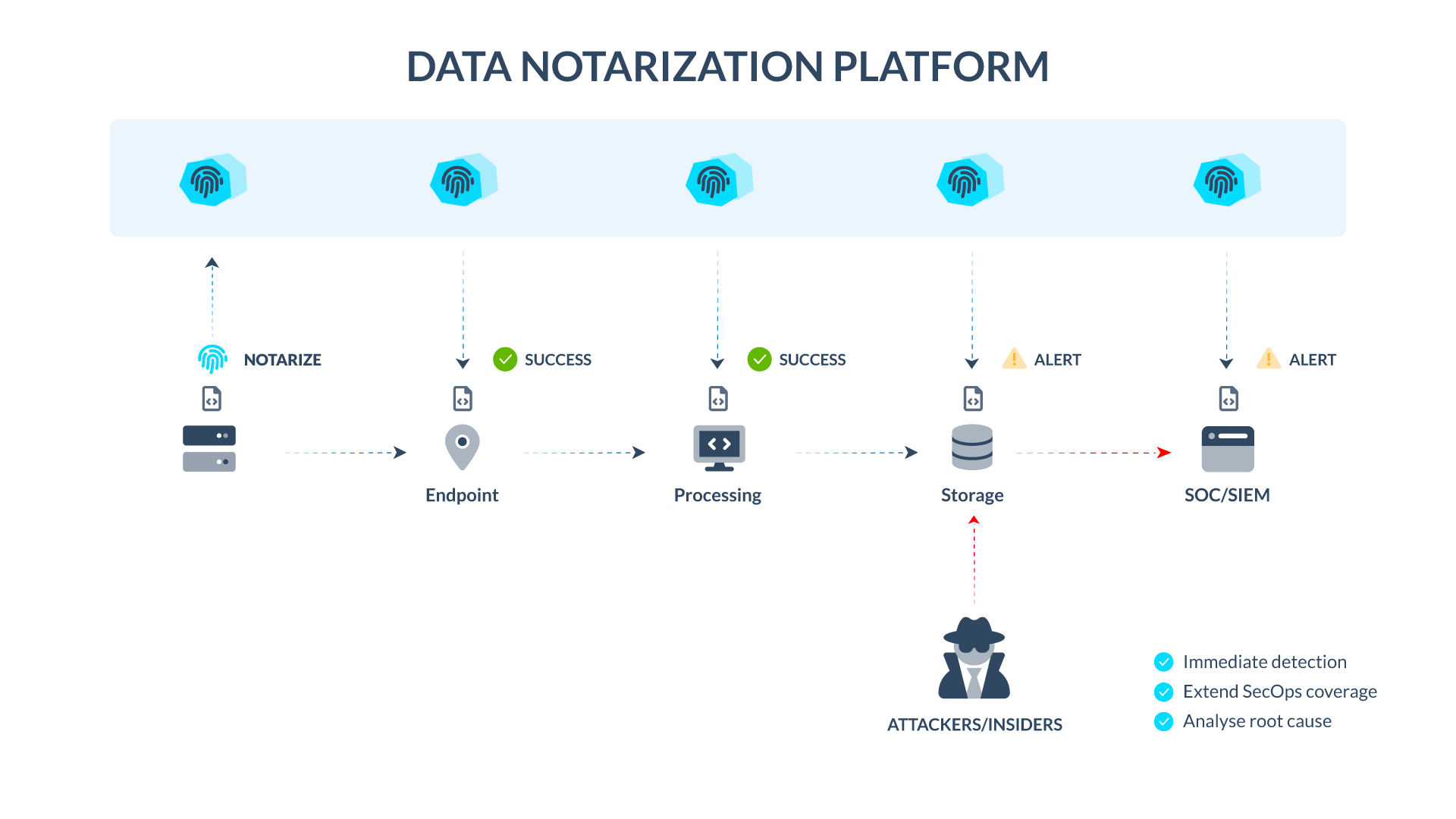
To protect log data from being tampered, Tributech’s Data Notarisation offers an end-to-end solution to secure integrity and authenticity of log data, without adding to busy workloads of security operation teams.
- Secured at source: Cryptographic proofs are generated directly at the data sources to protect integrity and authenticity, minimising the attack surface.
- Efficient and Scalable: The data notarisation platform provides an efficient and scalable solution to secure log data as it only stores cryptographic proofs within the immutable storage.
- Tamper-Proof: Cryptographic proofs stored in an immutable database cannot be modified, ensuring data integrity and authenticity.
- Detection: Log data can be verified on a recurring schedule and event based (e.g. an audit) to detect tampered data on a fine granular level, allowing organisations to detect and sort out bad data.
- Integration: The platform can be integrated with SOC/SIEM to provide ongoing data tampering detection as well as to support forensic analysis and external audits.
- Compliance: Data notarisation can help organisations comply with regulatory requirements, such as NIS2, DORA, HIPAA, and PCI-DSS, by providing a secure and auditable record of log data.





