Secure Web Gateway (SWG)
Secure web gateway (SWG) sits between users and the internet to filter traffic and enforce acceptable use and security policies on business devices. This includes the restriction of access to unsuitable or non work related websites, to not only increase security but also productivity.
You and your employees will remain protected whether on-prem, fully remote or hybrid.
Endida’s SWG solution replaces the traditional legacy SWG architecture which requires hardware (and policy is only enforced in the office), by moving policy enforcement from the cloud to on-device, this means that we are flying direct between your device and your internet access so you’ll experience a seamless, fast browsing experience.
SWG Features
- Content Filtering
- Application Control
- TLS/SSL inspection
- Stop Malicious Threats
- Data Loss Prevention (DLP)
Enforce user policies that control access to inappropriate or non-business-related websites (like social media)
Enforce policy on the usage of web-based apps and cloud services
Protect against malicious activities concealed within encrypted SSL/TLS traffic
Prevent users from downloading malicious software
Prevent loss or leakage of sensitive data
How can Secure Web Gateway enhance CyberSecurity?
Virtually every business now uses cloud-based applications, the adoption of cloud has partially or completely replaced some of the legacy physical and hardwired networks of traditional offices.
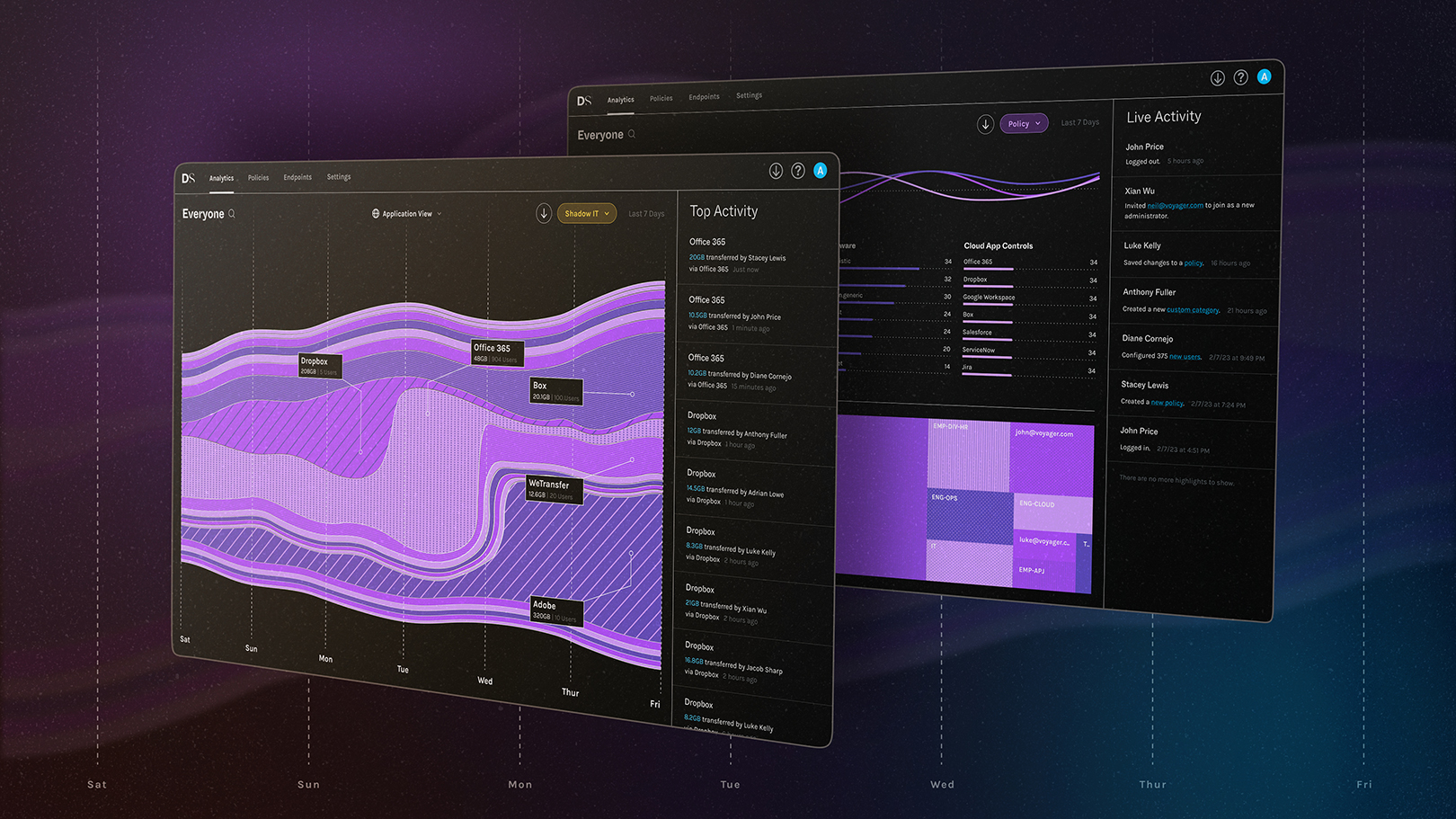
SWG is a security solutions that enforces access policies for websites, cloud resources and applications, providing visibility, policy control, analytics and productivity gains.
We all know that we can be attacked from the outside but in addition to this, we need to consider that our people themselves can be the weak link in security.
How can you automatically deploy policies so that your people are given the right authorisation to access the right places and send and receive content in a completely safe and controlled way?
Enforcing security policy
Be sure it is your employees and known devices accessing your cloud-based applications
Adaptive access control
Give access to the right data by the right people in you organisation rather than blanket access to everyone.
Data loss prevention
Put in place measures to ensure your data is not at risk from outside attackers or insider threats (disgruntled employees)
Behaviour analytics
Is an employee accession data or a cloud-based application they don’t normally have access too?
Automated Remediation
If any of the rules are violated or compromised, automatically shutdown access and investigate.
Productivity Gains
Prevent access to no productive sites and applications, including person Gmail, social media and even job sites.
The four cornerstone foundations of Secure Web Gateway
Visibility
Companies need visibility and control across both managed and unmanaged cloud services
Compliance & Policy
Regulatory, local and governmental compliance regulations are increasing for cloud-based applications
Data Security
Securing sensitive cloud based data such as employee records, accounting information, proprietary design data is becoming increasingly difficult.
Threat protection
Ensuring cloud based applications are sufficiently protected against outsider and insider threats is fast becoming the number one priority for any size organisation.
60%
Of the world's business data is stored in the cloud
Source: National Cybersecurity alliance
90%
Of global business use one or more cloud-based applications
Source: Gartner
200
Zettabytes of data will be stored in the cloud by 2025
Source: Cybercrime Magazine
76%
Of UK business feel their data is at risk inside cloud-based applications
Source: Forrester Research
The new era of increased remote working and use of cloud-based applications has driven a greater need for more complex security enforcement between users and cloud-based applications.
Key features of Endida’s solution
- Productivity – By setting policies around websites your employee can and can’t access, as well as preventing the use of streaming, social media and even access to personal Gmail means your corporate devices are only used for work
- Visibility – We monitor all of the cloud applications being accessed by users including any by your outsourced IT dept. This information enables us to build a risk assessment and form overarching security policy as well as controls for specific users and applications.
- Hybrid – Our enforcement engine will work no matter where an employee is located whether it is remote, office or on a business trip.
- Data loss prevention – Endida service will protect any data that is travelling to, within and stored in the cloud reducing the risks of costly data leaks.
- Threat protection – We use the data from typical user patterns to identify malicious behaviour and activities as well as negligent behaviour.
- Compliance – Endida helps ensure your organisation is compliant to regulations such as GDPR
- Agile access controls – Traditional security only allows you to either block or deny access, Endida’s Cloud-based application security service allows you to deploy the right of access to the right people
So does it work?
Our service starts with a full assessment and analysis of which cloud-based applications and websites you want to protect, how your users access them, and what devices they commonly use.
We can then deploy the right policies for individuals and groups of users.
Once implemented these policies can be monitored and automated giving you full control over unauthorised or malicious access
Get in touch to find out how we can help you today
Get In Touch© Endida 2024
Endida Limited




