Continuously find, fix, and verify your exploitable attack surface
Endida is one of the few licensed resellers in the UK, of the NodeZero Platform from Horizon3. Implementing NodeZero gives a continuous find, fix, and verify loop that empowers your organisation to reduce your security risk, by autonomously finding exploitable weaknesses in your network. It will then produce detailed reports and guidance about how to prioritise and fix all of the exploitable weakness – think of it as your own 24/7 Penetration Tester
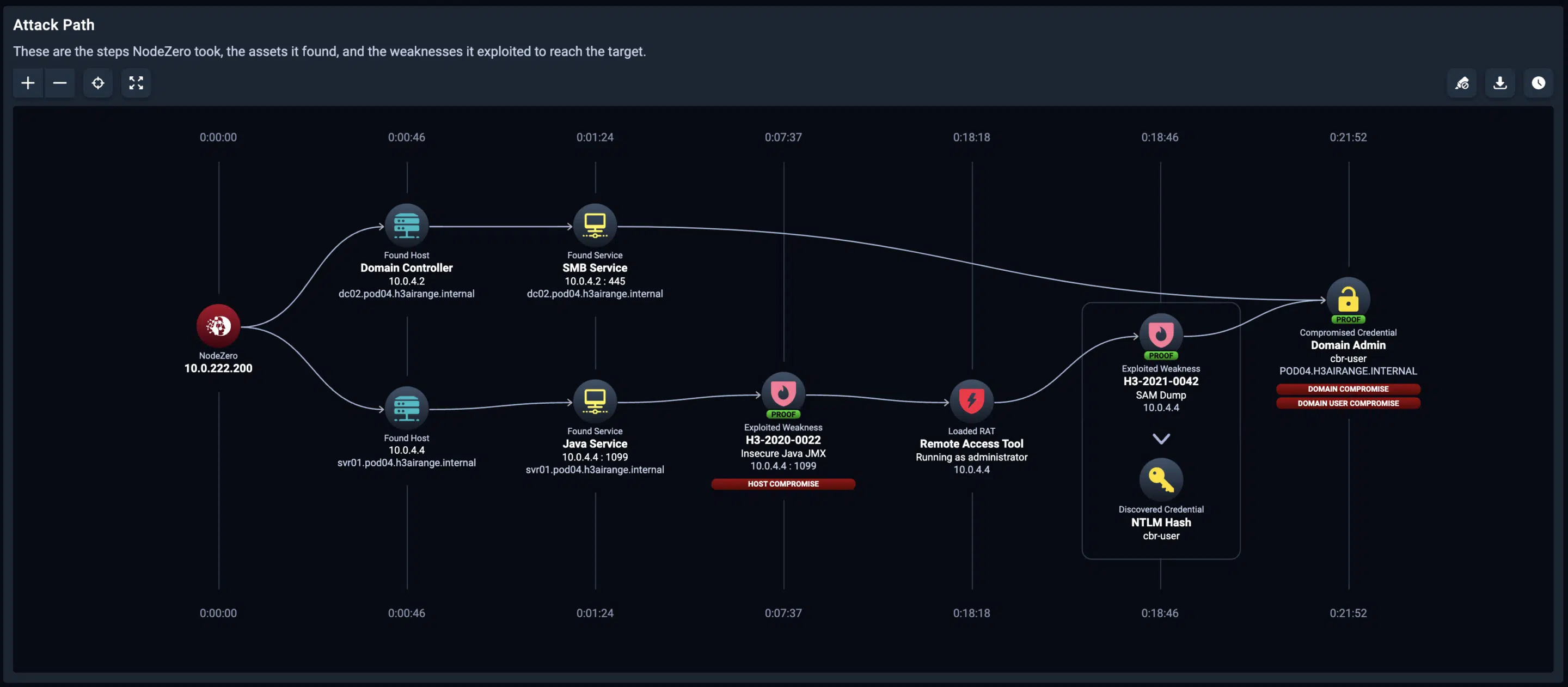 In this autonomous pentest attack path, NodeZero exploited two weaknesses — a Java JMX misconfiguration and SAM credential dumping — to achieve domain compromise.
In this autonomous pentest attack path, NodeZero exploited two weaknesses — a Java JMX misconfiguration and SAM credential dumping — to achieve domain compromise.
How The Platform Works
- Enumeration Test
- Deploy Docker
- Gaining access
- Maintaining access
- Analysis and reporting
Run an Enumeration test in the platform to discover your internal attack surface
Deploy the fully encrypted Docker container in your network, no need to 100’s of agents
Start exploitation of weaknesses and vulnerabilities & gain access to the devices on the network
Maintain access to the system or network for as long as possible to ensure all attacks are covered
Provide a detailed report outlining the vulnerabilities that were exploited and how to remediate them
Nodezero Penetration Testing Platform
The NodeZero Penetration Testing as a Service (PtaaS) platform enables your in house team to perform the most effective real world attacks on your entire IT infrastructure. NodeZero not only uncovers weaknesses, misconfigurations, leaked or compromised credentials, but also checks the effectiveness of your existing cybersecurity protection mechanisms – both hardware and software.
The full post-test report gives IT teams, CIOs, CISOs and SoC teams a detailed analysis of attack paths with evidence of exploitation and prioritised corrective actions.
NodeZeo Platform Testing Comparison |
||||
| NodeZero PtaaS | Manual Pen Test | Vulnerability Scan | ||
| Initial Penetration Test | 24-48 hours | 8 days (at least) | 3 days | |
| Included Re-Tests | Unlimited | One (limited scope) | Extra cost | |
| Exploit Vulnerabilities | Full path with proof | Partial – limited proof | No | |
| Default Config Credential Exploits | Full library | Limited | None | |
| External Pen Testing | Included & Unlimited | Additional Cost | None | |
| Advance booking Req | None | 60-90 days | 20 Days | |
| Deployment | One (Docker) | Long scoping call | Agent on every device | |
| Enumeration Test (Ports & Services) |
Unlimited | None | None | |
| Fix Actions Report | Extensive | Limited | None | |
| Credential Injection | Unlimited | None | None | |
| Latest CVE’s | Added Daily | None | Adhoc | |
| AD Password Audit | Unlimited | Extra Cost | None | |
| Phishing Penetration Test | Unlimited | None | None | |
| Pre-Schedule Test’s | Daily/Weekly/Monthly | None | Monthly | |
| N-Day Test’s | Unlimited | None | Adhoc | |
| Scalability | Unlimited | Hire more people | Unlimited | |
| Consistency | AI based | Open to human error | Software only | |
| Reports | Pen Testing Report Exec Summary Fix Actions Report Segmentation Report PDF & CSV Reports Enumeration Report |
Pen Testing Report Limited Fix Report |
Single report | |
Click to download an example NodeZero Pen Testing sample report
Click to download a sample Nodzero Fix Actions Report
64%
Number of organisations have experienced at least one successful cyber attack in the past year.
Source: Ponemon Institute International
$600bn
The annual cost of cybercrime to the global economy
Source: Center for Strategic and International Studies
84%
Number of organisations that conduct regular penetration testing and identify critical vulnerabilities.
Source: Association of Certified ISAOs
80%
Number of senior IT employees and security leaders believe that companies lack sufficient protection against cyber attacks.
Source: (ISC)’s 2021 Cyber Workforce report
How does NodeZero Compare to a Vulnerability Scanner?
NodeZero, compared to traditional vulnerability scanners, provides a more comprehensive security assessment by simulating real-world attack scenarios. This approach not only identifies vulnerabilities but also evaluates the potential impact and exploitability of those vulnerabilities in a real-world context, offering a more actionable insight for remediation. This method can be more effective in identifying complex security issues that might be overlooked by conventional scanners.
Not all vulnerabilities identified by scanners are exploitable in real-world scenarios. Vulnerability scanners often provide a list of potential security weaknesses based on known vulnerability databases and patterns. However, the context, configuration, and specific environment in which these vulnerabilities exist can greatly affect their exploitability. Some identified vulnerabilities may be theoretical, mitigated by other controls, or not applicable due to specific system configurations, making them non-exploitable in practice.
Benefits of the NodeZero Penetration Testing Platform
Accuracy
Autonomously test and help you fix problems that matter, saving you time and money
Effort
NodeZero is up and running in hours, not weeks, our fully certified Horizon3 team we do all the work for you to ensure you are testing within a few days
Speed
No need to wait weeks or months for consultants to manually run pentests and produce reports - NodeZero will enable any IT or SoC team to testing within a few hours of implementation
Coverage
NodeZero will cover your entire internal and external network - it even works with IoT Devices and Cloud storage too.
Remediation
NodeZero automatically creats actionable, curated reports to enable your team to quickly find exploitable problems, fix them and then verify that the problems no longer exist
Privacy
The platform is exclusively yours to use, not multi-tenant or sharing
Does it really work?
NodeZero uses the latest autonomous technology to drive the penetration test platform. The platform is so thorough it often finds multiple issues with weaknesses and credentials – a manual pentester will usually stop when they find a single issue with a particular device or service. NodeZero will find all of the assets you want to pen test and all that is needed internally is a simple docker container
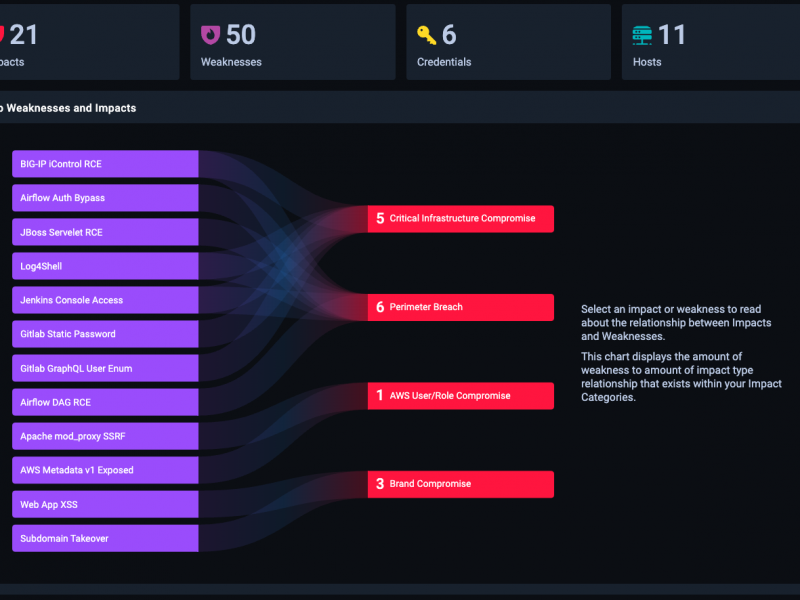
Benefits of Nodezero for Penetration testing COMPLIANCE
Scope of Testing
- Unlimited, Continuous Testing
- Internal Network Pen Testing
- Website and External IP Testing
- Cloud Pen Testing
- Remote & Hybrid Working
- Virtual Machine Pen Testing
Credentials & Compliance
- Can be Crest Certified
- Google Pen Test Complaint
- Microsoft Pen Test framework
- NHS Digital Compliant
- NIS2 Compliant
- DORA Threat Lead Pen Testing
Frameworks
- Test Against Latest CVE’s
- Overall Security Posture Score
- Mitre Att&ck Framework Testing
- Custom Pen Testing Framework
- Exec & VIP Out of Office Risk
- Windows, Linux, Mac, IoT & Docker
QUESTIONS? HERE ARE THE ANSWERS
Penetration testing is a process of testing computer systems, networks, and applications to identify vulnerabilities that attackers could exploit. It involves simulating real-world attacks to determine the effectiveness of an organisation’s security defences.
Penetration testing can help organisations identify vulnerabilities and weaknesses in their security defences before attackers can exploit them. It can also help organisations meet compliance requirements and improve their overall security posture.
The types of pen testing include network testing, web application testing, mobile application testing, social engineering testing, and wireless network testing
Endida’s autonomous penetration testing uses tools and AI to scan systems for vulnerabilities and exploits without the need for time consuming human intervention.
Automated testing simply automates certain tasks, it does not “think” like AI does.
Manual pen testing involves actual human testers who use their knowledge to identify vulnerabilities, however this is limited to their own training & knowledge. They may miss something if they do not know it is an issue.
The frequency of pentesting should be determined by factors such as the organisation’s risk profile, the sensitivity of its data, and the nature of its operations. Generally, organisations should conduct pen testing at least once every 6 months and after any significant changes to their systems or networks.
Some common challenges with penetration testing include false positives, lack of resources or expertise, and resistance from stakeholders who may view the testing as a disruption to their operations.
With Endida’s service, all of these issues are eliminated.
Penetration testing involves simulating real-world attacks to identify vulnerabilities and assess the effectiveness of an organisation’s security defences. Vulnerability scanning is an automated process that identifies known vulnerabilities in systems and networks but does not test the effectiveness of security controls.
After a penetration test, the experts here at Endida will present you with a full, in-depth report along with recommendations as well as the professional services needed to fix them. We then prioritise and address the vulnerabilities identified, develop a remediation plan, and conduct regular follow-up testing to ensure that the vulnerabilities have been addressed.
Get in touch to find out how we can help you today
Get In Touch© Endida 2024
Endida Limited




