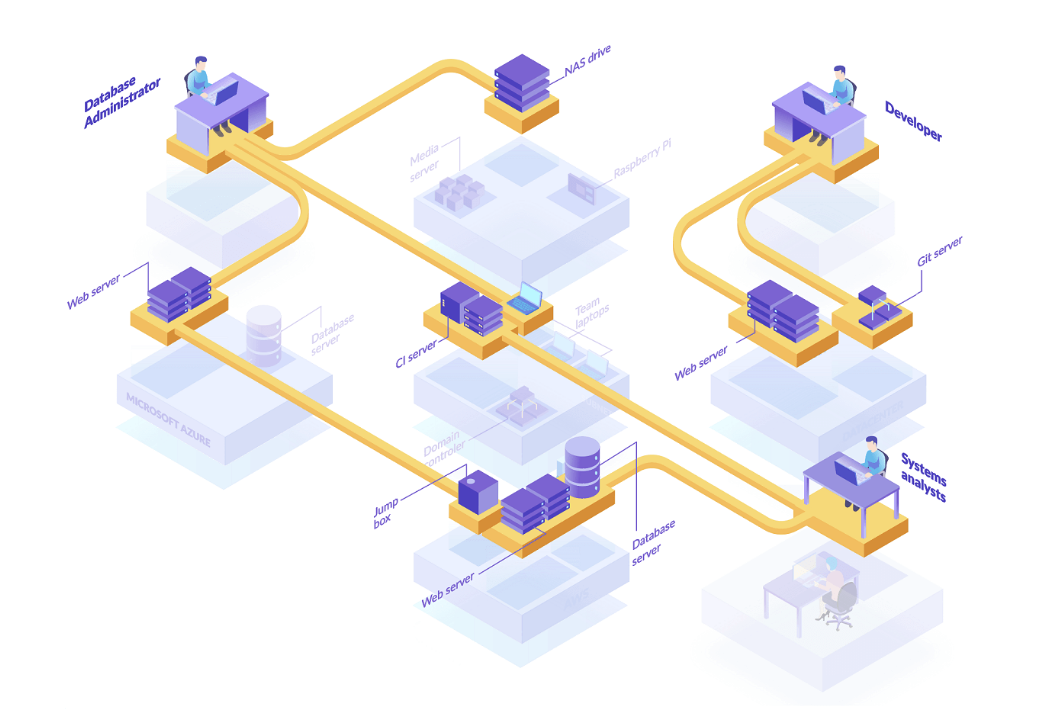
Secure Enterprise access to anything, from anywhere
Replace outdated, hardware based VPN Servers with a modern private access solution based on Zero Trust Principles that simpler, easy to install and manage plus a lot more secure.
- Direct Connectivity
- No Firewall Config
- Policy-Driven Connectivity
- Extremely Quick Rollout
- End-to-End Encryption
- Wide Device Support
No hardware VPN servers to install and no having to connect to the VPN, “always on” policy based availability
Firewalls stay closed, no need to open ports or have expensive reconfigurations
Create access policies for individual devices or entire gateways, fully control access and authentication requirements – you can even add time limits (temporary access)
Roll-out in minutes – register device, allocate a key, create policy and you are done
Fully encrypted traffic no matter where the connection is made
Windows, Linux, MacOS, Android, iOS, Docker, Kubernetes all fully supported
Endida’s ZTNA Solution
Endida’s ZTNA solution delivers secure network access through dynamic, policy-based authentication, ensuring only verified users and devices can access specific resources. It assesses identity, device health, and access context in real-time, granting the least privilege necessary. This scalable, flexible approach supports remote work by integrating with corporate and cloud infrastructures, enhancing security while simplifying user access.
Endida’s ZTNA Comparison |
||||
| Endida ZTNA | Traditional VPN | |||
| Trust Model | Never trust, always verify | Full trust on single authentication | ||
| Open Firewall Ports | 0 | 20-30 | ||
| Access Control | Granular, user & context dependent | Broad, grants full network access | ||
| Required Hardware | None | Multiple appliances/racks | ||
| Security Posture | Enhanced, continuous verification | Initial authentication only | ||
| User Experience | Seamless, zero user intervention | Cumbersome with complex logins | ||
| Resource Accessibility | Access to specific resources | Access to the entire network | ||
| Scalability | Immediately highly scalable | Extra hardware & full project | ||
| Attacker Visibility | Invisible to attackers, no open ports | Insecure to operate with open ports | ||
| Traffic Movement | Devices speak directly | All traffic through VPN hardware | ||
| Connectivity | Tunnels created when needed | Always on | ||
| Low-ops | No network adjustments needed | Complex configuration | ||
| Precision access | Lateral movement prohibited | Lateral movement enabled | ||
| DNS | Built-in DNS | No native DNS support | ||
| Dynamic IP tolerant | Works seamlessly | ACL’s/advanced IP knowledge | ||
WHy USe Zero Trust Network Access?
Zero Trust is relatively straightforward in that, instead of building castle walls around your network and defending that perimeter against outsiders, you assume that no system or endpoint, either inside or outside your castle walls, should be trusted by default.
As team members are increasingly operating outside our premises, we need a different approach to assigning and managing trust and affording access to our critical network infrastructure.
Zero Trust Network Access (ZTNA) takes nothing for granted; identities must always meet trust standards, access must be provided only on a need to know basis, systems need to be micro-segmented and continuously checked, verification and trust must be established, not assumed.
Why Endida's ZTNA & VPN Replacement is Superior
Easy Deployment
Non-disruptive deployment, Endida works alongside existing solutions. Install on one, or one thousand devices without rip and replace, and roll out easily via RMM without additional hardware or proxies to deploy.
Simple Configuration
Endida's intuitive visual policy engine is delivered in a non-technical, cloud-based management platform which makes it simple to arrange private access, and easy to reason about the state of the network.
Precision Access
Building one-to-one connections, Endida’s ZTNA solution cloaks your applications with invisible network access gates which only materialise when certain trust standards are met to protect against discovery, targeting and attack.
Use Cases for ZTNA
Privileged Access
Grant access to System administrators and DevOps teams
Multi-Cloud
Private Access. Any application. Any infrastructure. Any network. Anywhere
Remote Working
Replace your VPN with a modern private access solution that’s simpler and more secure
Third Party and supply chain connectivity
Effortlessly connect with partners, third parties and your supply chain
VPN replacement, without the rip.
Deploying Endida’s Zero Trust Network Access to replace traditional VPN servers can help you succeed in a variety of scenarios.
Our easy to deploy solution makes it simple to replace old VPN servers incrementally, one system at a time if necessary, to quickly upgrade your customers to modern private access without needing to rip out their existing infrastructure first.
A Zero Trust approach mitigates many of the risks associated with traditional VPN connectivity. VPNs work on the basis that they’re freely accessible to anyone on the public internet. If someone maliciously manages to authenticate themselves through your remote access VPN server, then they are inside your castle walls and can move around freely.
Traditional Hardware VPN
- All Traffic moves through VPN Server
- Slow to arrange connectivity
- Manual enrolment, setup and tear down
- Insecure to operate with open ports
- Risk of lateral movement
Endida’s ZTNA solution
- Devices talk directly to one another, fast path selection
- Quick to arrange connectivity, low-ops network as code
- Automatic enrolment, setup and tear down
- Invisible to attackers, no open ports
- Zero Trust networking with precision access.
Endida's ZTNA Solution
© Endida 2024
Endida Limited